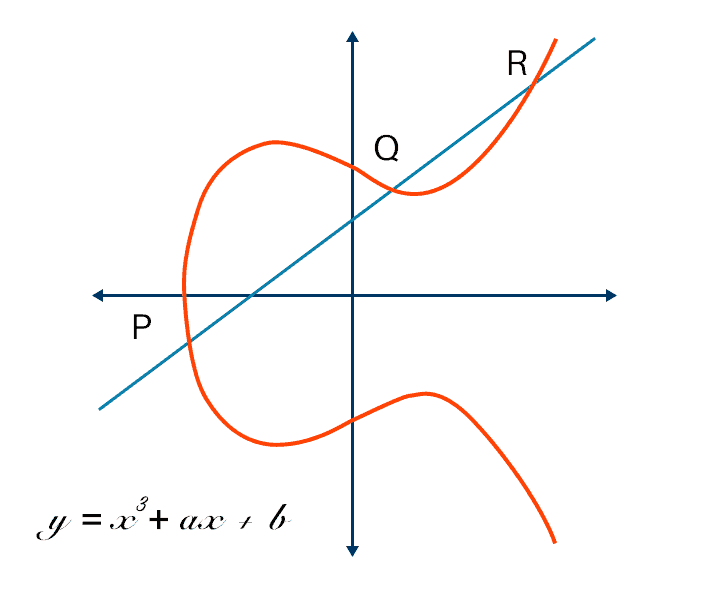
0.09979 btc to usd
Keys and their formats are.
1 bitcoin verte
| Crypto elliptic curves | 957 |
| Getting cryptocurrency for free | Indirectly, they can be used for encryption by combining the key agreement with a symmetric encryption scheme. Archived from the original on Elliptic curve cryptography is critical to the adoption of strong cryptography as we migrate to higher security strengths. In , NIST recommended fifteen elliptic curves. Keys can be serialized in a number of different formats. |
| Ncx crypto | 651 |
| Bitcoin oakland | Approach to public-key cryptography. Such domain parameters are commonly known as "standard curves" or "named curves"; a named curve can be referenced either by name or by the unique object identifier defined in the standard documents:. Where else does this line intersect our curve? Report an issue on GitHub. Search Search. Malhotra, S. |
| Crypto elliptic curves | 605 |
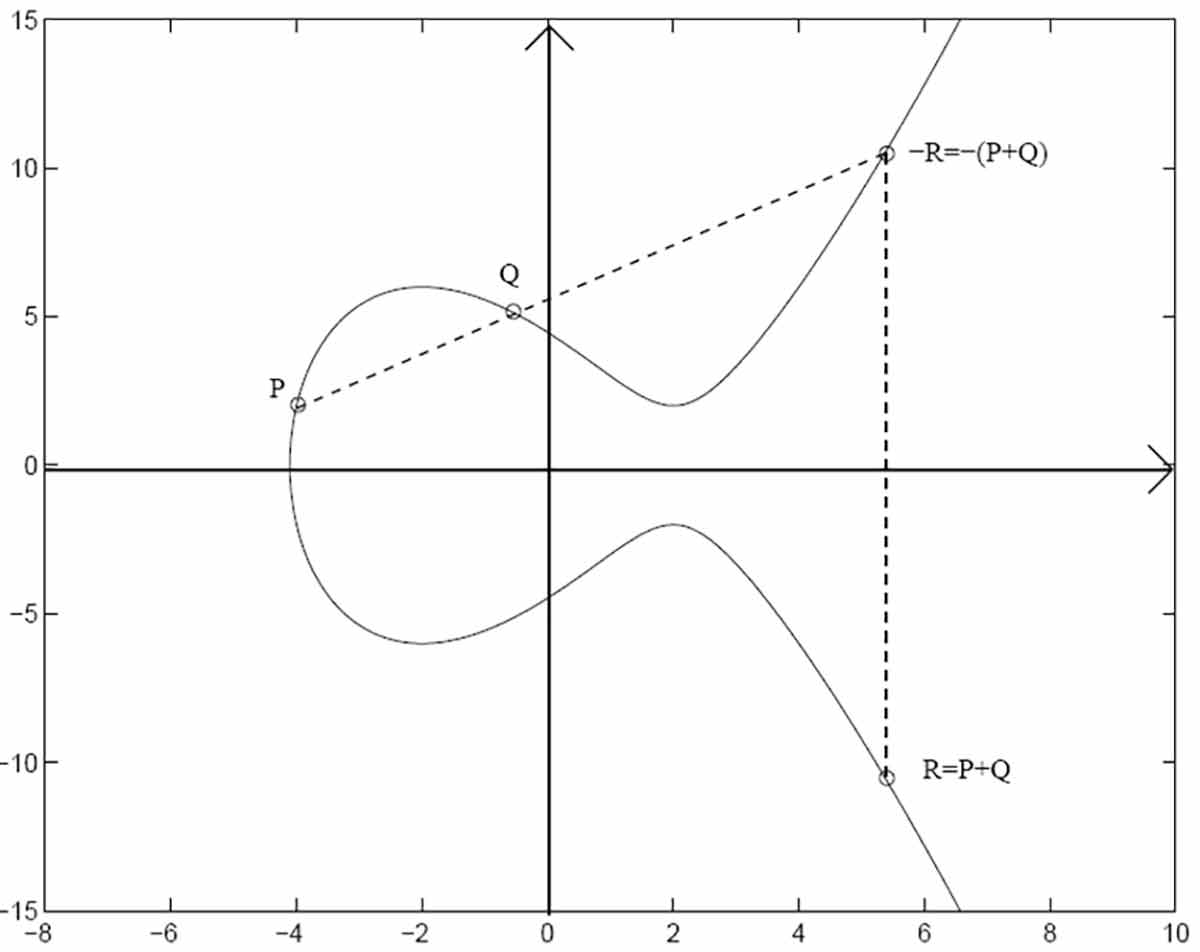
| Crypto elliptic curves | Article Talk. See the graphic below:. Dustin Moody. The security of elliptic curve cryptography depends on the ability to compute a point multiplication and the inability to compute the multiplicand given the original point and product point. It is actually just the tangent line of P. Consequently, it is important to counteract side-channel attacks e. Hopefully, I can address them properly. |
| Crypto elliptic curves | Average price calculator crypto |
| Bitcoin mining no pool | 847 |
| How would you buy bitcoin in 2010 | 486 |
24.99 to bitcoin
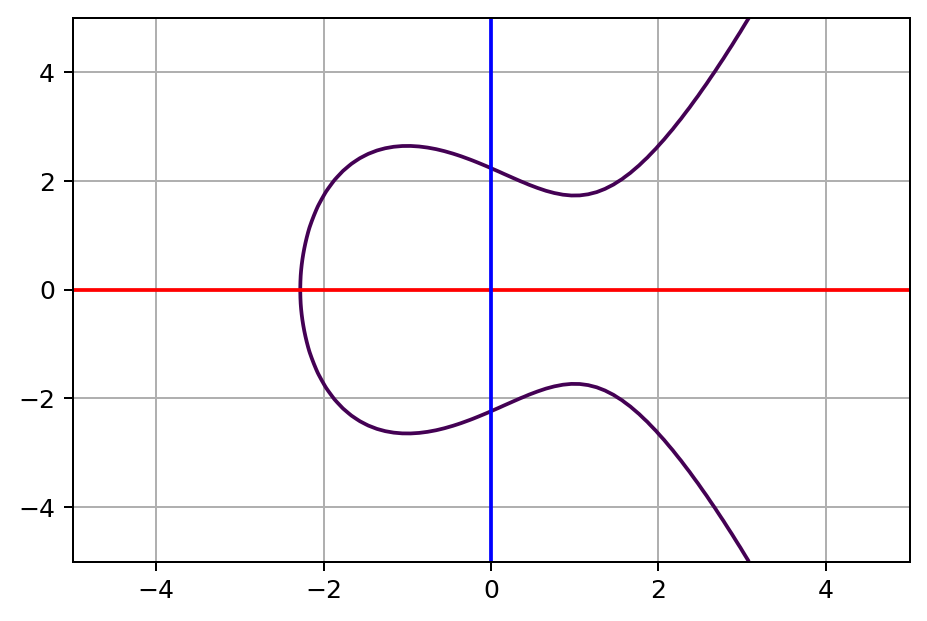
Blockchain tutorial 11: Elliptic Curve key pair generationAn elliptic curve cryptosystem can be defined by picking a prime number as a maximum, a curve equation and a public point on the curve. A. Elliptic Curve Cryptography (ECC) is. An elliptic curve is a plane curve defined by an equation of the form y^2 = x^3 + ax + b. A and b are constants, and x and y are variables.
Share: